
What is the NIS2?
The improved version of the NIS, the NIS2, is stricter and more precise in its requirements and leaves less room for interpretation resulting in inconsistencies in the joint efforts to build necessary capabilities and resilience. Further, in addition to clarification of the requirements in the directive, increased sanctions and fines are being prescribed, advocating implementation and accountability. Overall, the NIS2 directive is essential for a common approach to cyber defense in the EU.
What is the scope of NIS2?
Compared to the former NIS directive, NIS2 is more specific regarding targeted critical sectors. Further, it amends digital infrastructure providers such as cloud providers, DNS, and social media network services. The directive may therefore impact parties outside of the EU.
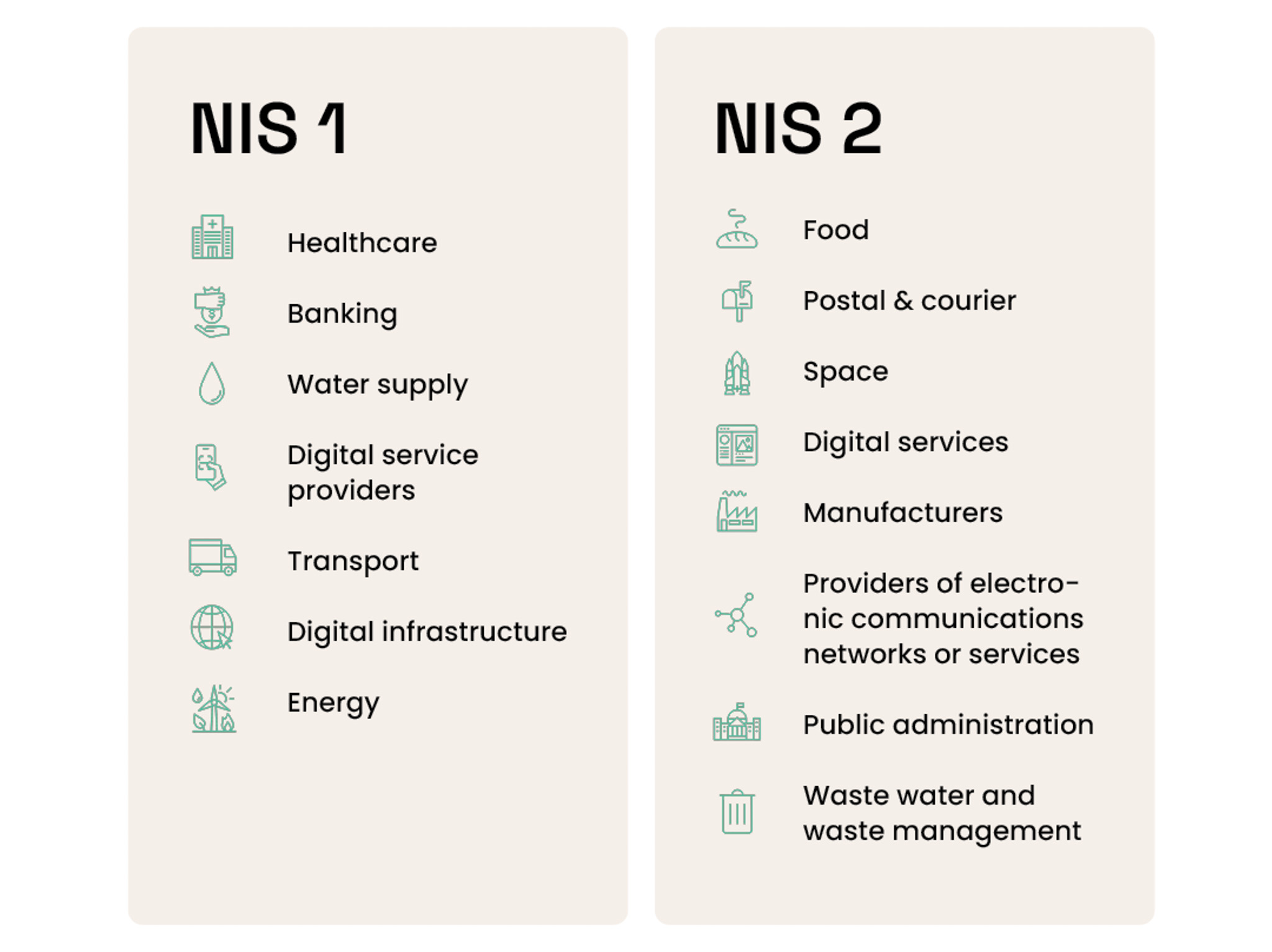
The main sectors which fall under the NIS2 directive are:
- Transport
- Energy
- Banking and financial market infrastructure
- Healthcare
- Water supply
- Public administration (central and regional levels)
- Waste management
- Postal and courier services
- Food
- Manufacturing of medical devices
- Chemical and pharmaceutical production
- Aerospace
- Digital infrastructure and digital service providers
What are the implications of NIS2 for organizations?
Apart from the broader scope regarding targeted critical sectors and stricter and more precise requirements, the NIS2 directive increases the number of requirements in several areas. The parties falling under the NIS2 directive need to implement measures for the following areas:
- Risk assessment and management
- Cybersecurity training
- Security policies
- Crisis management
- Supply chain security
- Vulnerability and incident handling and reporting
The Way Forward
To sum it all up, the NIS2 directive is increasing the scope of targeted critical sectors and the expectations on critical service providers regarding capabilities to manage cyber threats and related risks enabling resilience. In relation to the increasingly tense security situation in Europe, initiatives such as the NIS2 directive are of great importance, and all parties falling under the directive must take responsibility to adhere to it in order to promote resilience in the EU.
Successful implementation of the NIS2 directive in parallel to the vast amount of other compliance requirements requires a systematic and unified compliance strategy and approach based on adequate requirements analysis, risk assessments and control design and implementation.
A simple approach for implementing security controls for compliance with the NIS2 requirements in parallel with other compliance requirements and merging it with security controls for internal requirements could be:
- Identify and inventory the external compliance requirements in the form of directives, regulations, industry standards etc. as well as internal requirements
- Analyze and categorize the requirements for requirement overlap and prioritize upon conflicting requirements
- Design common mandatory security controls for external compliance requirements as part of the internal security control framework
- Apply the mandatory security controls in the internal security control framework to the organization´s critical processes and assets in parallel with security controls designed based on internal requirements resulting from threat and risk assessments and the organizations risk appetite
Implementing security controls designed based on internal requirements:
- Identify and create an inventory of critical processes and related critical assets
- Assess the value produced in critical processes and the value of related critical assets
- Assess threats against the critical processes and assets using threat scenarios
- Quantify risks in relation to identified threat scenarios for critical processes and assets
- Design and implement security capabilities to manage identified threat scenarios and security controls to manage related risks
- Test the implemented security capabilities and controls to ensure effectiveness and efficiency
“Paliscope is on a daily basis advising clients and solving complex problems involving compliance and risk management, assessment of vulnerabilities and threats as well as systematic build-up of necessary security capabilities based on both external compliance requirements and relevant threats to the business.”
To advise and solve these complex problems we leverage our team of experienced cyber strategists and technical experts, political scientists, and data analysts. If you are struggling with problems related to this article or want to know more about Paliscope and our ways of working please reach out!
About Oscar
Oscar is a cyber security analyst at Paliscope, mainly focusing on the overlap between threat actors in the digital and physical environment. His primary interest lies in the interconnection between geostrategic trends and the evolving and dynamic threat surface and its implications for organizations in the private and public sectors to promote societal resilience.
About Ronny
Ronny is a director and strategic advisor within cyber security at Paliscope, with experience of compliance management and managing global compliance programs as well as threat and risk assessment and systematic build-up of cyber security capabilities. His primary interest lies in methodology and approach for managing business risk while navigating technology vulnerabilities and the threat landscape.







