Warren Bulmer is a digital investigator and was one of the expert witnesses for the Crown Counsel in the Amanda Todd sextortion case.
Between November 2021 and the trial in June 2022, he authored various reports numbering a few hundred pages. There were all in response to prosecution requests to provide or present evidence to the jury in the trial. Many of these reports needed to explain how computers connect to the Internet and what IP addresses, VPNs, proxies, and cookies are.
In addition, the reports had to discuss how Facebook worked and how it had evolved between 2010 and 2013 because that was the time period these activities occurred.
The final and most important piece was to analyze 13 Facebook accounts and their associated records. Each of these accounts, the prosecution alleged, participated in the offenses committed against Amanda Todd in one way or another.
Warren’s job was to find the commonalities or connections between those accounts using various methods and present them to the jury.
The challenges confronting the Truth Hounds and other investigative entities in Ukraine are multi-faceted. One immediate hurdle lies in the sheer volume of data and information accessible from open sources, including social media platforms. Additionally, ensuring that online-collected evidence adheres to established digital evidence frameworks, as prescribed by the International Criminal Court and the European Union Agency for Criminal Justice Cooperation (Eurojust), poses another challenge.
VICTRAS decided to move from manually processing and analyzing their data, to implementing Paliscope Explore and Build.
Processing all their incoming and existing data in Explore made it possible to overview and search through any information they had. They could now easily cross-reference new information with existing intelligence to find possible correlation with previous cases, and thus progress the investigation much quicker.
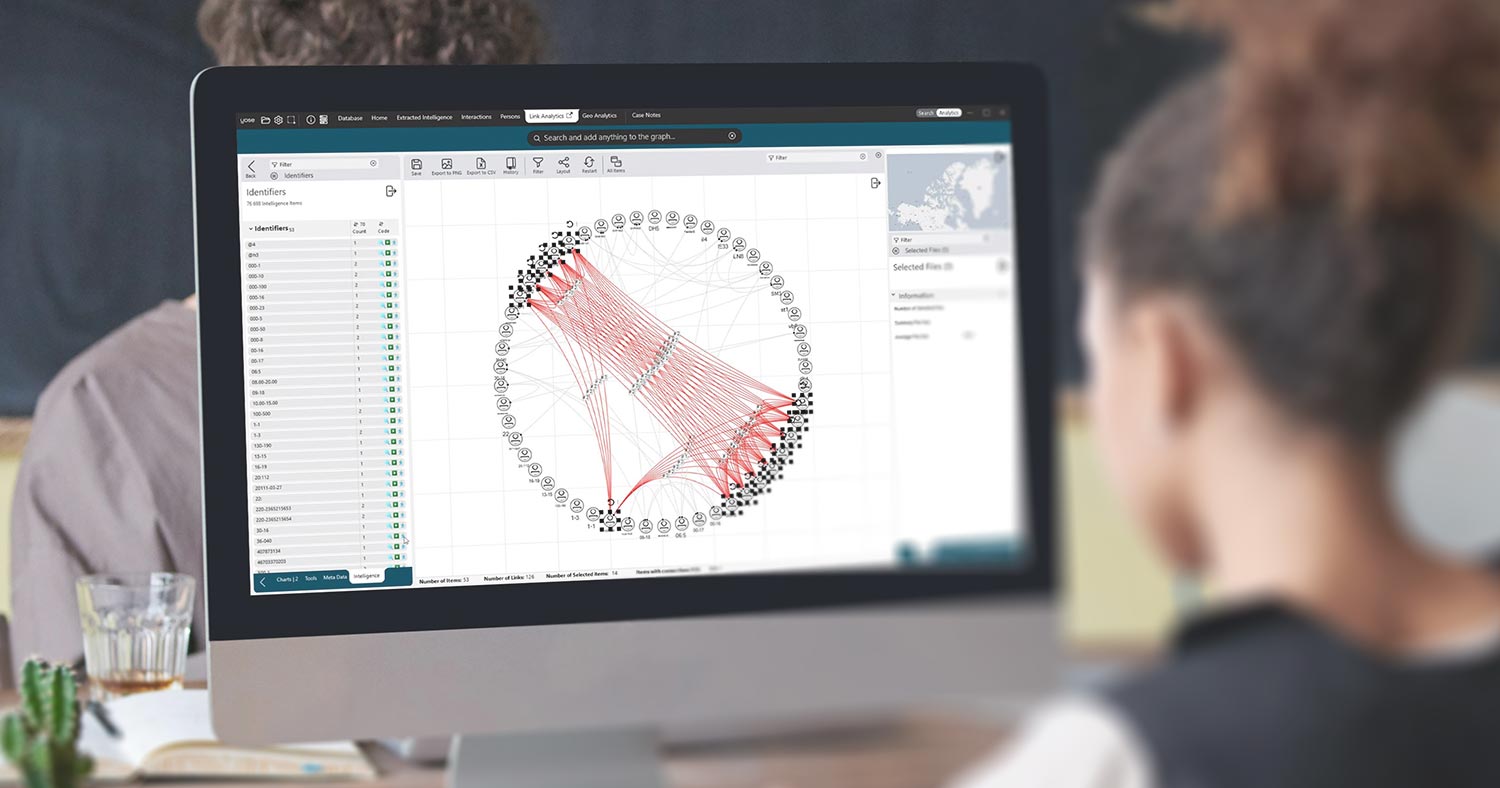
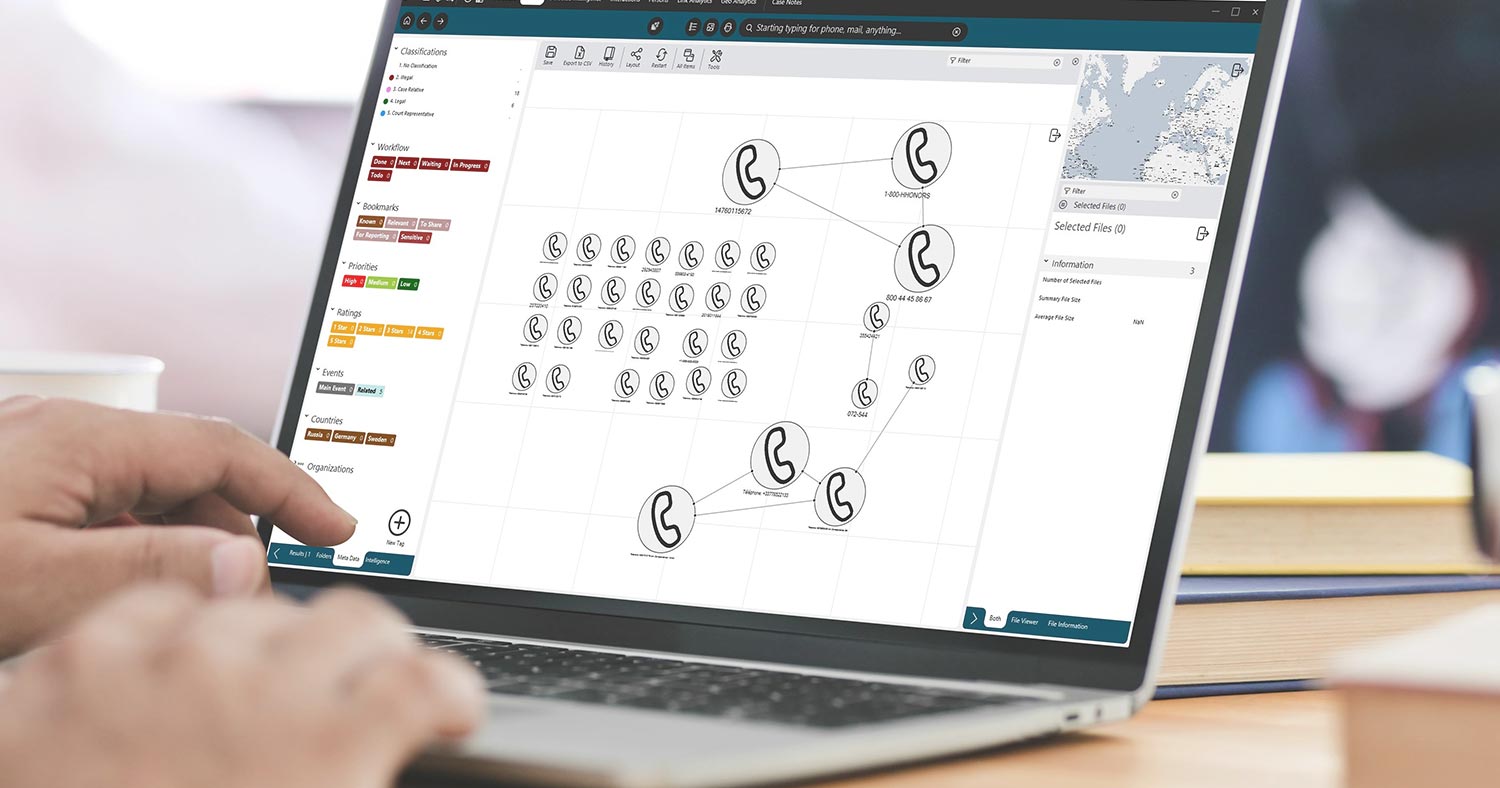
Using Explore’s powerful link analytics they immediately identified connections through shared contacts, telephone numbers and aliases, as well as through visual connections like being seen on the same images or videos. Explore’s abilities to handle any type of data, enabled them to find clues and links practically impossible to do manually.
In their data, they found that the trafficker had multiple connections with a previously investigated criminal group that runs so called connection houses on the route from Nigeria to Europe. They could also identify a shared bank account connecting them to a Madame (the manager and person receiving the victims in Europe) and further more finding where this Madame was located.
Warren has been involved with the development of Explore and has good knowledge of its tools and features.
For this case, he needed the ability to isolate a certain set of artifacts, the session activities specifically, and analyze connections or similarities between them. This meant he needed to focus on hundreds of session activities between the 13 accounts.
In the trial materials provided to him by the prosecutor, there was an Excel spreadsheet that they had prepared prior to bringing him on board. It was a part of their preparation of the evidence, and it contained a summary of just over 1,460 session activities from all of the accounts in question.
The columns included IP addresses, dates and times, account names, machine cookie values, locations (derived from the City, Region, and Country), and some photo uploads. All this data was imported into Explore, which structured the information and made it searchable.
He created a book for each account, and the general contents for each book described any Facebook artefacts they had in common with the other targeted accounts in question. Then, wherever he found matching data, he outlined what the connections were. Explore helped him find the connections, which he verified in the Facebook records.
The final area Explore assisted him with was in using the ‘Comparative Analytics’ feature. There were two accounts that had a lot of artifacts in common. They had a total of 171 unique machine cookie IDs combined. He needed to know how many of those intersected between the two accounts. Explore showed him they shared 53 machine cookies, 46 of which were unique values.
Using Explore, he could analyze a large amount of data and find crucial connections. He used Explore to structure the information and evidence presented in court.
Paliscope Explore created an opportunity for me to visualize the data. One piece of information can be valuable, but when you can connect 2 or 3 pieces, it becomes powerful, and it can change the level of coincidence.”
n December 2020, Aydin Coban was extradited to Canada to face prosecution for his sextortion of Amanda. On August 6th, 2022, he was convicted of all charges.
On October 14th, 2022, he was sentenced to 13 years in prison.
Many other investigators and experts were working on the case and also prosecutors who did an outstanding job. Everyone contributed with their skills, knowledge, and determination to putting Aydin Coban in prison for a long time. And we are proud of the part we could contribute to with Paliscope Explore.
READ MORE: The pursuit of justice for a young girl, a guest blog by Warren Bulmer
This intelligence was handed over to the police who later conducted a raid on the suspected address. The case was then confirmed when many exploited women at the location were already known by VICTRAS. Having documentation of the route and events these victims had been through substantially eased the process going forward for both the police and the young women. They could be put to safety and out of the hands of whom they had been controlled by.
No need to worry about evidence documentation and report formatting. Paliscope Build automates all that - keeping your cases structured, secure and easy to hand over.
Find what you are looking for with Paliscope Explore - enabling analysts and investigators to triage large amounts of data and deep dive into the findings.
Process all your data in one place, collaborate across teams, search for anything, and more.