Working with digital investigations in today’s environment is hard. No matter if you are working with digital forensics, online investigations or as an investigator lead you’ll need to juggle a constantly changing landscape. How do you keep track of new digital tools? How do you handle complex legal aspects that might ruin your case if not handled correctly? Last but not least, how do you write a report that makes your findings come across without misunderstandings?
Luckily we’re here to help.
In this article we talked with Joseph Jones on how you can avoid the 5 most common challenges in digital investigations. Joseph is a former British Intelligence and a former UK National Crime Agency officer.
After reading this article you’ll have a better understanding on how to solve challenges regarding

1. Documentation – Saving time to catch criminals instead
When it comes to documentation one big challenge is time. Since you have to be able to use your investigation as evidence, it needs to be documented in certain ways, and in a certain order to hold up in court.
Documentation can also be highly stressful for investigators, due to the risk of being cross examined in court if the job was poorly done.
Evidence must be the way you found it
To use data from your digital investigation as evidence, you have to show proof that the file is exactly the way you found it. Which means that no one has modified the evidence.
Time stamps or hash values?
Joseph explains that in Nordic countries law enforcement agencies use time stamps, url and screen shots to secure evidence. In the US for example they have to put a hash value on all data they find. Many investigators are expecting this to spread to other countries as well.
A Hash Value is a fixed string of numbers and letters, generated from a mathematical algorithm. This generated string is unique to the file being hashed.
If the file is altered in any way, the hash value changes and the evidence is not to be trusted.
Hash files manually is time consuming
To “hash” files manually for every evidence you find is time consuming, and in any investigation having time for actual investigative work is really valuable.
Manually hashing is also considered insecure based on the fact that evidence such as a HTML file can be saved, altered and then hashed.
So how can you avoid manual work and still document your investigation in a safe way?
Unfortunately there are no easy work arounds. To make this part of the job more efficient and safe we suggest you use a system that does the work automatically.
There are multiple investigation systems out there. For example, if you use Paliscopes product Discovry for collecting evidence, the system will automatically timestamp and hash all evidence. It also creates a protected audit trail making it easy to follow the chain of custody in the investigation.
Not only does this allow investigators to save time and use that time to develop further lines of investigations, it also guarantees that evidence cannot be tampered with from the moment it is collected from the source and presented in the report.

2. Reporting – A time consuming job for digital investigators
One of the biggest challenges for digital investigators is the time spent on making structured and well communicated “easy-to-read” reports.
Reports are amongst other things used as evidence in court which means that it’s important that the information it contains is accurate, well structured and easy to use.
“To make proper reports is very time consuming if you do it manually. Investigators we´ve worked with have told us that in big cases it can take weeks to structure all the information into one report”, says Joseph Jones.
No easy quick fix for reporting
We wish we could give you an easy quick fix to this problem, since we know many digital investigators struggle with this part. But we can’t think of another solution other than using our own system in this case.
To make automated reports is one of the most important tools we have in Discovry.
When you use Discovry to collect evidence, the system automatically structures all your data into easy-to-follow reports.
It means time that investigators would normally spend copying, cutting and structuring data into a document manually, can now be directed towards detecting and monitoring other criminals instead.
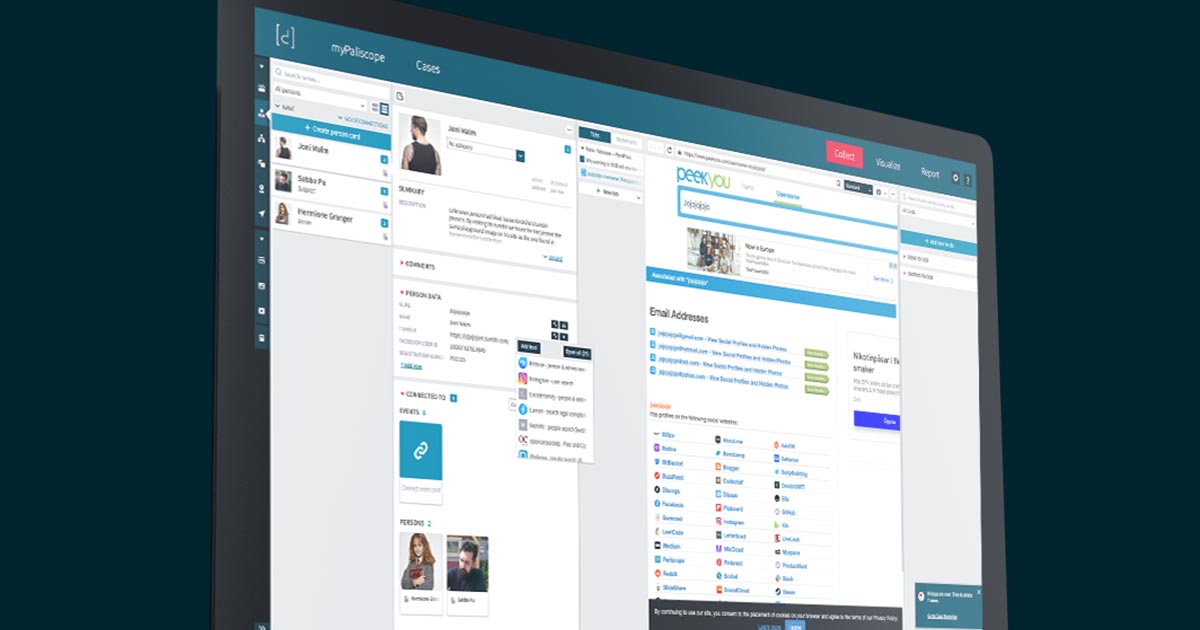
3. Tools – The importance of keeping yourself updated
Another challenge for people working with digital investigations is that the web is always changing. That means that online tools you use may work one day, but the next day they’re outdated and useless.
Social media platforms for example make updates constantly. When Facebook removed the Graph Search function, it affected all digital investigators since they could no longer search for specific information about people or places.
To help you we have written an article about 3 Facebook search workarounds everyone is talking abou
Additionally, there is a significant range of investigative tools available, knowing which one to use and when to use it can be a time-consuming process in its own right.
So how can you make this part of the job easier?
One thing you could do is keep yourself updated by reading blogs written by experts in digital forensic investigations.
Here are some blogs about OSINT (Open Source Intelligence) that we really like.
They share a lot of useful information about tools, tactics and techniques for digital investigations. There are also a couple of online courses which you can take any time you want.
OSINT Curious
The OSINT Curious Project is a source of quality, actionable, Open Source Intelligence news, original blogs, instructional videos, and live streams. Here you can keep yourself updated with new techniques to access important OSINT data.
OSINT Combines training
This is an Advanced Open Source Intelligence Course. The course teaches you how to collect, analyze and produce high quality reporting based on advanced Open Source Intelligence collection.
Jakes Creps
On Jakes Creps you can learn more about the latest open source intelligence OSINT tools, tactics, and techniques for your digital investigations.
Bellingcat
Bellingcat is an independent international collective of researchers, investigators and citizen journalists using open source and social media investigation to probe a variety of subjects. They frequently describe how their investigations are performed and what type of tools they use.
Sans
Sans is a digital platform for education in cyber security. They have many different courses you can go to. We recommend SEC487 – Open Source Intelligence Gathering and Analysis.
“If you work in a big organisation, it might be a good idea to share new tools to your teammates so you’re all up to date with the latest tools and techniques.“ says Joseph.
In Discovry for example we have taken that part of the job one step further to make it easier keeping yourself and your team updated.
We have created a feature called “Tools” which makes it easy to share useful investigation tools around the organisation.
With a quick click of a button, you can easily search for a specific data type and automatically be presented with results from the corresponding tools. This feature allows you to search through different sources at the same time.
This is something that will help you quickly track down the information you are looking for and, hopefully, solve more cases faster.

4. Safety – Leave no fingerprints behind
For your own safety, and for your organisation, it is important to know how to investigate online without leaving digital fingerprints. You don’t want anyone to discover you since it can severely complicate further investigation.
Here are some things you should know about:
How cookies works
A cookie is a more friendly term to describe a tracker – but in reality, it’s function is to track user behaviour.
Whilst most cookies are harmless, some can be used to gather information about you. At the same time, some online services are known to use cookies to create a profile about you and your online behaviour.
Each time you visit a website, that website may store a cookie on your computer – via the browser. When you revisit the same website, your browser sends the information back to the site.
The problem with cookies is that there is a potential risk of being discovered by criminals. Cookies can give away the fact that you are investigating something, which could interfere with your investigation.
So how do you keep cookies from contaminating your investigation?
Block cookies in your browser
One solution is to block all cookies from your browser. You do this by going to settings in your browser, find preferences for cookies and check the “block all cookies” box.
The problem with this solution is that many websites rely on first-party cookies to provide basic functionality. By blocking all cookies, you may find that you can’t use many important websites at all, or they will have reduced functionality.
Use investigation software
Another solution is using a system that is made for investigations. In Discovry for example we keep your cases in separate cookie containers, separating the cases from each other, which means that information does not leak from one case to the other.
Use VPN to anonymise your IP address
Lastly, the use of a Virtual Private Network (VPN) and a Virtual Machine (VM) can also provide you with anonymity, ensuring that cookies which are stored on your system refer to an anonymised IP address.
However, as should be best practice at the end of any investigation, the browser and system must be cleared of Cookie data before the VPN is switched off.
How social media works
Social media platforms are designed to connect people. But they are also used by social media companies to track user behaviour and measure user interests.
For Law Enforcement, social media is a valuable source of intelligence against criminal suspects as it allows investigators to potentially obtain information regarding a suspect’s movements and their inner-circle.
However, the information that can be obtained via social media is very much dependent on the privacy settings that suspect’s have implemented. As such, information that is not publicly visible cannot be obtained, though some countries have systems where warrants can be issued to social media companies to provide private user information.
Important: Use a “Sock Puppet” on social media
Investigations conducted on social media should be done through the use of a fake social media profile – also referred to as a ‘Sock Puppet’.
However, when taking into account that social media companies collect user behaviour, it is very important to ensure that Sock Puppet activity is done through a VPN and is consistent in-terms of searches and general behaviour.
For example, a Sock Puppet that was created and accessed in Sweden being used to investigate criminals in the United Kingdom can be flagged.
READ MORE: How to build a solid fake identity for online investigations.
What browser you should use
What browser you should use very much depends on what your digital investigation needs to achieve.
For example, some Social Media Intelligence (SOCMINT) investigations require tools that may only be available on Mozilla Firefox. At the same time, certain web forensic activities require Google Chrome-based extensions. For Dark Web investigations, most activity will require the use of Tor.
We know this can be complex since there are so many different systems and browsers. But don’t forget these important rules:
1. Use a clean computer and software
Regardless of what system or browser you use to conduct your investigation, the most important consideration is the need to be digitally secure with a clean computer and software which has not been compromised from previous activities.
2. Use a dedicated computer for investigations
It is important to use a dedicated computer for the sole purpose of digital investigations which means; no personal usage and no unnecessary activity.
3. Use anti-malware and VPN
In addition, investigators need effective anti-malware software and a trusted Virtual Private Network (VPN) solution.
In Discovry for example you have access to two browsers. A a clearnet browser similar to the investigation browser Brave and the darknet browser Tor. These browser are good to use for online investigations and are made for reducing your fingerprint.

5. Legal aspects– Keep updated with GDPR
Legal considerations vary depending on your organisation and the purpose of the investigation. For example, Law Enforcement are required to comply with legislation that may not necessarily apply to an insurance company.
Joseph says it’s hard to give a “one fits all-solution” to legal challenges. But one thing all organisations acting in the EU have in common is the legal requirement to comply with GDPR.
If you work with digital investigations it might be hard to know exactly what parts of GDPR that are relevant for your work. Therefore, your organisation should have an experienced Data Protection Officer (DPO) who can develop and maintain GDPR compliance.
An example of something regulated in GDPR is how long you are allowed to store data. It is important to make sure you don’t hold on to data any longer than necessary.
It is a good idea to have a system where you can keep track of important information like this, since it can be a costly mistake to be found in breach of Data Protection.
So what systems can you use to comply with GDPR?
An example of a company who is working with GDPR is Aigine. Aigine reads all information from all data sources and uses unique self-learning AI to identify, legally assess and document personal data in order to ensure true privacy compliance and automated governance.
Discovry has some neat features that takes this challenge into account. All data collected within Discovry is stored locally and it also has a feature which lets you flag data for deletion after a set amount of time. It will remind you when you need to remove data, and when you are finished with the case you can choose to delete all related files from your computer.
We hope this article has given you some useful tips that you can use when working with digital investigations.





