How to recognize and prevent extortion emails – the most common form of cyberattack.
By Rikard Bodforss, CyberSecurity Expert and founder of Bodforss Consulting
Extortion emails are a common tool criminals use to threaten heavy damage to a person’s privacy, and demand payment in return for inaction. Here, you can find some tips and tricks on how to recognize these types of emails and prevent them from ending up in your inbox in the first place.
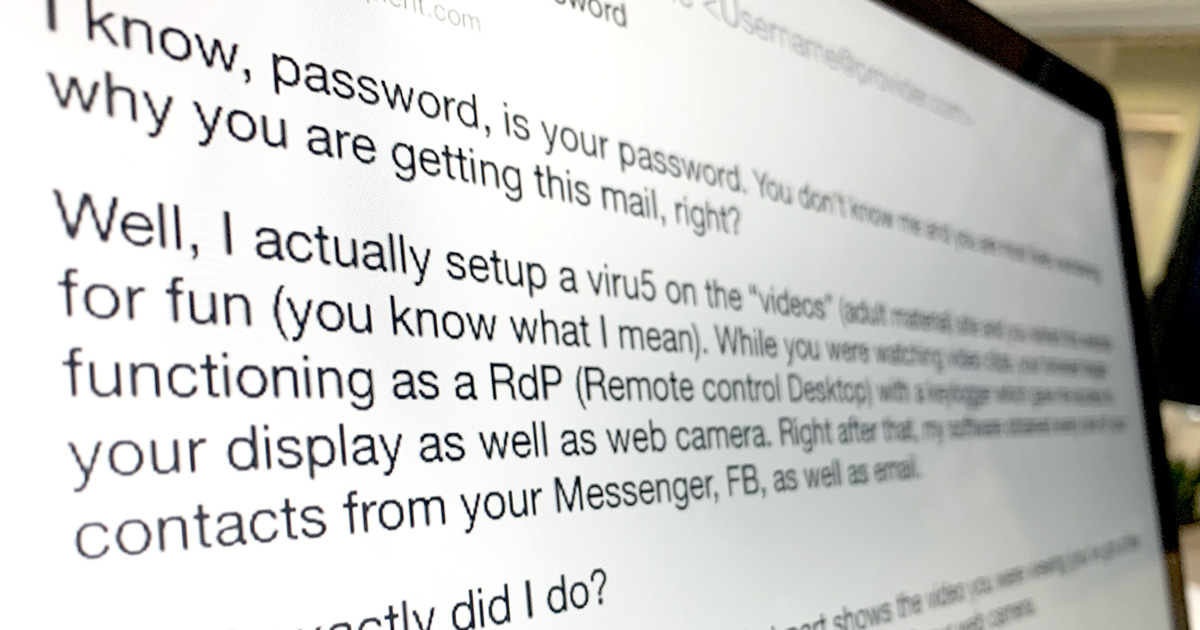
One of the most common types of scam emails, and something going around a lot right now, is “sextortion” scam emails. These are emails claiming, “We’ve been monitoring your online activities for several months now and while you visited X porn site we hacked your computer and recorded you through your own webcam. This video will be sent to all your friends and family if you do not pay X amount of dollars to this account within 48 hours.”
When an email like this lands in front of you, it’s easy to panic. While it can be difficult, as a private person, to figure out whether it’s fake or not, you can most always assume that the extortionist is bluffing. A thorough investigation would indeed require professional help. Something that few choose to invest in due to the expensive price tag. That’s why we’ve collected a bunch of tips here on how you can independently determine, step by step, whether or not the extortion email you have in front of you is fake.
Common to all fake extortion email is that they are auto-generated. They don’t have one specifically selected recipient, but rather the person on the receiving end of such an email has had the bad luck of ending up on a large list of email addresses for all sorts of people. Everything is about volume and, unfortunately, it is very easy to get hold of bulk email address lists in places like the darknet. So, just like you get an annoying marketing campaign email you didn’t sign up for, you can have the misfortune of ending up on lists for extortion schemes.
Two types of email extortion tactics
All extortion emails follow the same template—they are built in an almost identical way. This is because extortionists have found a formula that works. But there are generally two different ways they try to prove that they have managed to hack your computer and can therefore extort you for money.
The first tactic is that the email clearly states that your computer has been hacked and that the extortionist has access to your password, whereupon a password is presented in the email. It is almost always a password that you have actually used on one or more occasions. Since many people have the same password for different sites, this is a trick that gives the email higher credibility and leaves the person on the other side feeling afraid. It’s the feeling that they know everything about you. This is not proof that they have taken over your computer, even if the password is the same as one you use on that computer. Most likely, the extortionists have come across a list of passwords and email address from a hacked website.
The other tactic is that the email appears to have been sent from your own email address. However, this is only possible if you have used your email address in a domain that is not correctly set up with protection when it comes to which mail servers can send from the email address. This extortion trick adds to the feeling that the hacker is inside your computer.
“…it’s all just empty threats playing
off against your vanity.”
In nine out of ten cases, the sender also wants you to pay in cryptocurrency, usually bitcoin. If it weren’t for this, probably more people would pay. Furthermore, the email can often contain links that you’re asked to click on in order to get more proof. This is called a “phish hook.” If you click on a link, and have a traceable browser, you actually risk getting hacked for real. So never do it.
Unless you have actively chosen to participate in so–called webcam sex, where you have opted to switch on your own webcam during the session, the risk of someone having a compromising video of you is negligible. The odds are probably better of finding intelligent life on the dark side of the moon than of someone possessing embarrassing footage of you. These types of scams are just that, scams. To date, no one has received any compromising footage of any friend or family member, so it’s all just empty threats playing off against your vanity.
3 ways to spot and verify an extortion email
If you receive an unusual email and feel uncertain about whether it is a scam or not, here are a few things to look at.
1. Strange links. Hover over any links in the email to see if they match their supposed destination (once again, never click on them!). If you are interested in getting more information about the linked webpage, visit https://www.getlinkinfo.com. This tool lets you view information about a link without having to click on it.
2. Have I been pwned. On the site https://haveibeenpwned.com you can search your own email address to find out if you are included on sites that have been hacked. The vast majority of people are actually included. You can even place your email address under watch and receive notifications directly if a site where your email address is listed gets hacked. If your password was included in an extortion email you received, it probably came from a hacked website and you are likely included on this list.
In the case that your password for other sites is the same as the one you have for the site that has been hacked, change your password immediately.
3. Bitcoin abuse. On the site https://www.bitcoinabuse.com you can see if any previous transactions have taken place with a specific bitcoin wallet and also if someone else has reported it. This is a good way to detect and confirm that the payment being demanded is a scam.
Protect yourself from extortion emails
1. Always use different passwords. Or, to make it even easier, use a password manager. For example, 1Password or LastPass. Even if it does not mean 100% security, it’s still significantly safer than going without. Furthermore, it is much easier because you can collect all of your passwords in one secure place and log in to different sites and domains with a single click.
2. Use a good anti-malware program. To reduce the risk of falling victim to scam emails in general, it is always good to install an anti-malware program. For example, Kaspersky, F-secure, Norton, McAffee, or Eset. If you use a Mac, we can also recommend Little Snitch which is a firewall that protects against certain types of trojan viruses. Another good thing to install is anti-spam protection, which reduces the risk of receiving scam emails. Anti-spam protection is already included in email services such as Gmail, Outlook and Hotmail.
3. Never click on anything or respond to the email. This is something that especially applies if you have already been subjected to scam email. But we cannot emphasize enough how important it is to not click on any links, since doing so can lead to you really being hacked.
So, what do I do when I receive an extortion email?
To summarize your immediate actions in one word: Nothing. Read through this article again, at least three times. Then go over your online hygiene and make sure you change any compromised passwords that may be exposed in an extortion email. While you’re at it, get a password manager and have unique passwords for each site. Even better, enable two-factor authentication on all accounts that are sensitive (like your primary email account).
Whatever you do, do not click on any links, or respond or interact with the criminals. Feeding the troll will just pull you deeper into their net, and soon you’ll be like a fly trying to wiggle out of a spider’s web. Once you are convinced that it is a scam (trust us, it is), just delete the email. There will probably be follow–up emails, but they’ll soon lose interest. After all, it’s just an automated marketing system responding to a preconfigured action plan. Rest assured, it’s all fake. At least until you click on any links in the email.







