The Threat Landscape
Hostile actors in cyberspace increasingly utilize the complex supply chains on which most modern organizations depend. Consequently, the threat landscape is growing as these are often well-needed. Still, complex networks of suppliers create broadened attack surfaces which enable alternative access points for malicious actors. Put shortly, weakly defended service providers unintentionally offer a potential perpetrator opportunity to circumvent defenses of its primary target, i.e., a customer of the supplier, which brings severe implications for supply chain security in general.
Even though targeted attacks often require significant preparation, several attacks are often opportunistic and result from attackers undertaking broad sweeps of numerous organizations to identify vulnerabilities. For example, such methods might include automated internet scanning that identifies a poorly defended supplier, then successfully attacks that supplier and leverages their accesses into other organizations. Furthermore, the risks of a weak supply chain are becoming increasingly evident after the Russian invasion of Ukraine in February 2022. Since then, we have seen an increasing trend of supply chain attacks and various pro-Russian threat actors seeking access to target networks. Apart from increasing incentives among pro-Russian threat actors to conduct offensive operations targeting Western organizations, the conflict brings other types of supply chain vulnerabilities which need to be understood and managed accordingly.
First
The growing geopolitical tensions in Europe incentivize Russian actors to conduct espionage operations targeting its Western opponents. Such operations are potentially enabled through the supply chain, as attackers may target third-party suppliers or vendors with weaker security controls to access a target organization’s network.
Second
The ongoing war can disrupt supply chains for European organizations that rely on technology outsourcing or partnerships with Ukrainian companies. Disruptions can occur due to infrastructure damage, power outages, or other factors that impact the availability and reliability of services provided by Ukrainian vendors.
Third
The war can result in regulatory uncertainty and changes in local laws and regulations, which can impact compliance risks for European organizations operating in or partnering with Ukrainian companies.
In sum, the increasingly hostile environment requires organizations to understand the cyber security risks in their supply chain and develop adequate measures to identify, assess and manage them.

Cyber Supply Chain Security
Supply chain security is the part of supply chain management that primarily focuses on the risk management of external suppliers, vendors, logistics and transportation. Its goal is to identify, analyze and mitigate the risks inherent in working with other organizations as part of a supply chain.
Supply chain security involves physical and digital security relating to products and cybersecurity for software and services. Cyber supply chain risks may include the insertion of counterfeits, unauthorized production, tampering, theft, insertion of malicious software and hardware, and poor manufacturing and development practices in the cyber supply chain.
In this setting, cyber supply chain security involves minimizing the risks inherent in using software and hardware developed by external vendors and securing organizational data accessed by another organization in the supply chain. For any actor aiming to protect digital assets, it is crucial to understand that the software they use or purchase may not be secure. Therefore, adequate assessments and monitoring of internal and external supply chain entities are essential to promote security in the digital environment.
“Adequate assessments and monitoring of internal and external supply chain entities are essential to promote security in the digital environment”
Overall, the range of supply chain entities that may present cyber security risks is not limited to those who provide information and communications technology (ICT) services or infrastructure but may occur from any part of an organization. Therefore, supply chain cyber threats are an organization-wide challenge that points to the need for an adaptable response drawing from an iterative and agile approach to identify, assess and manage cyber security risks in the supply chain and encompassing technological and human risk factors to manage the growing threats.

Questionnaires and traditional approaches to mitigate cyber supply chain risk/promote supply chain security
Traditional approaches to cybersecurity in general and supply chain risks in particular, often focus on known vulnerabilities and threats. From this information, security measures are developed, such as physical security, firewalls, detection systems, and questionnaires.
Questionnaires are commonly used in the struggle to handle cyber supply chain risk. In short, questionnaires are often used to assess the security practices of third-party vendors or suppliers that provide critical technology services or products to an organization. More specifically, organizations use questionnaires to evaluate the security practices of their third-party vendors or suppliers. For example, these questionnaires may cover access controls, data protection, incident response, and disaster recovery. The answers to the questionnaires can help organizations identify potential security weaknesses or gaps in their suppliers’ security practices and take appropriate steps to address them.
Furthermore, questionnaires are used to identify high-risk suppliers that may require additional scrutiny or oversight due to the criticality of their services or products. For example, suppose a supplier handles sensitive customer data or provides critical infrastructure services. In that case, the organization may want to conduct a more in-depth security assessment or require the supplier to implement specific security controls.
Moreover, questionnaires are used for transparency purposes. Organizations can promote transparency and communication around cybersecurity risks and concerns by sending questionnaires to vendors or suppliers. Such methods can build a culture of security awareness and encourage suppliers to take appropriate steps to improve their security practices.
Apart from questionnaires, organizations may conduct on-site audits of their vendors or suppliers to assess their security practices and identify potential vulnerabilities or weaknesses. On-site audits involve physically inspecting the supplier’s facilities, systems, and processes to identify security risks and assess the effectiveness of their security controls.
Organizations also use contractual obligations to ensure that their vendors or suppliers meet the organization’s security standards and comply with relevant regulations or industry standards. Contractual obligations can include requirements for specific security controls, regular security assessments, and incident reporting.
“The growing threat landscape pinpoints the need for more agile approaches to secure one’s digital supply chain”
However, even though these measures may create a decent security posture or at least a sense of security, the growing threat landscape pinpoints the need for more agile approaches to secure one’s digital supply chain. Such measures inevitably require knowledge, commitment, and, naturally, resources.
Here, a dilemma emerges. Every organization that seeks to protect its operations from harm needs to assess their needs and capabilities vis a vis the threats it might face. The dilemma is often multifaceted and derives from these assessments, i.e., the likelihood and the potential impact of an attack and the resources needed to build an adequate defense. Moreover, as organizations increasingly rely on third-party vendors and suppliers for critical products and services they cannot develop in-house, their cyber risk profile becomes increasingly complex and challenging to manage.
Hence, when trusting external actors to provide efficiency in the supply chain, flawed assessments may increase the threat surface as suppliers may not have adequate cybersecurity measures to protect against cyber threats.
To address this dilemma, organizations need to leave the explicit focus on traditional security approaches and implement an iterative and agile approach to cyber supply chain management. Such an approach includes:
- Identifying and assessing the cyber risks associated with each supplier.
- Implementing appropriate security controls to mitigate those risks.
- Monitoring supplier cybersecurity practices continuously.
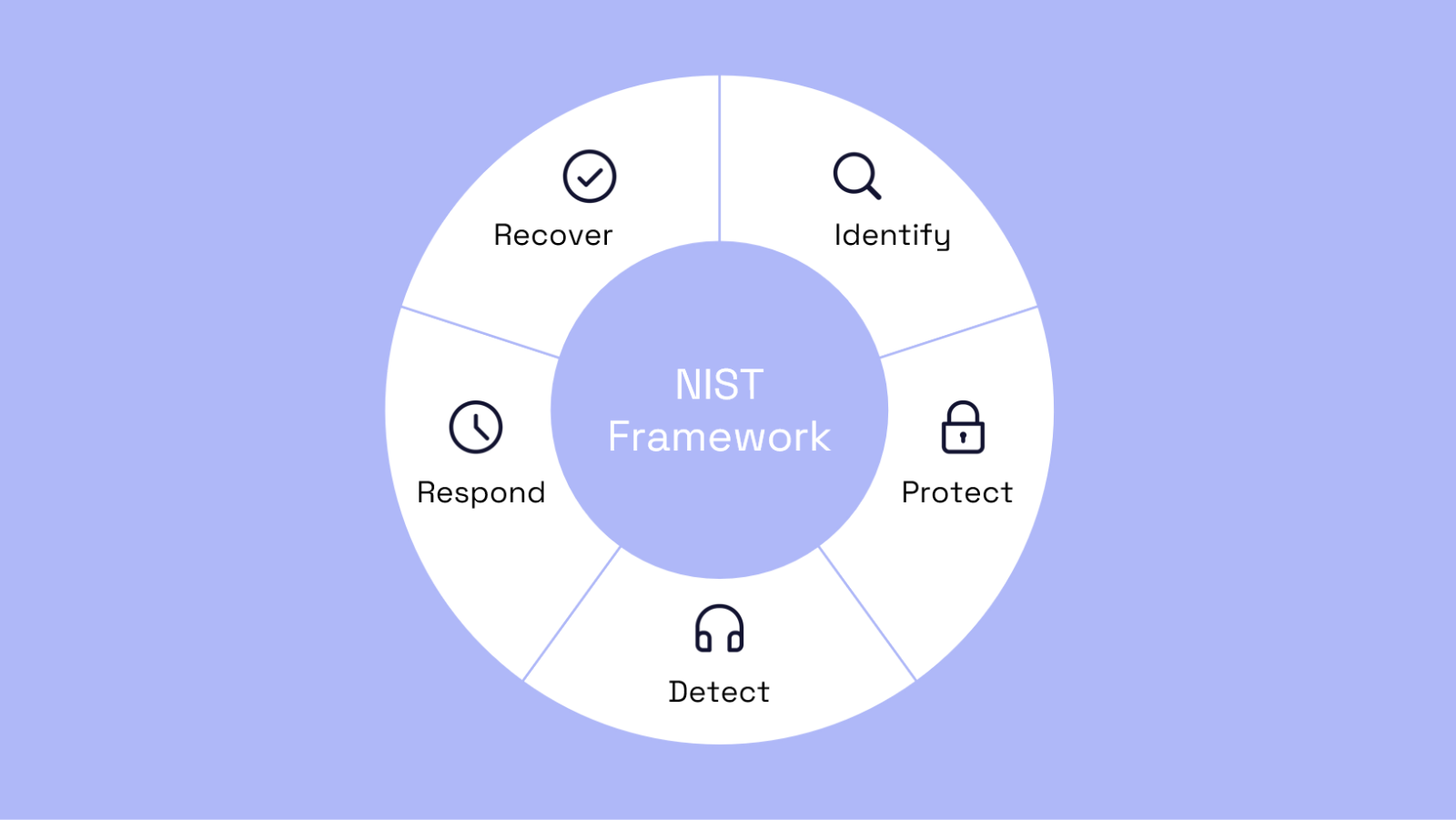
Organizations may also consider using standards and frameworks, such as the NIST Cybersecurity Framework, to guide their cyber supply chain security efforts. Apart from the NIST Cybersecurity Framework, there are other iterative and agile approaches to cybersecurity that we recommend, including:
- DevSecOps: DevSecOps is an approach that integrates security into the development process from the beginning. It involves collaboration between developers, security professionals, and operations teams to identify and address security risks throughout the development lifecycle.
- Continuous monitoring: Continuous monitoring involves collecting and analyzing data to identify potential security risks and vulnerabilities. This approach lets organizations quickly detect and respond to security incidents and adapt security measures in real time.
- Threat modeling: Threat modeling is a process that identifies potential threats and vulnerabilities to an organization’s assets and systems. It involves a systematic analysis of potential attack vectors and the development of measures to mitigate those risks.
The Way Forward
While there are no 100% guarantees in securing digital assets and protecting them from harm’s way, organizations in private and public sectors must take the steps necessary to maintain and develop adequate security capabilities. Evolving trends in the threat landscape points to an increasing need for a shift towards more adaptable and agile capabilities to handle cyber supply chain risk.
Paliscope works continuously to assist in these matters and help organizations acquire the tools necessary to develop resilient and flexible systems depending on their specific needs.
One such step is our continuous monitoring services, improving our client’s ability to manage their cyber supply chain. We will help safeguard your organization in the interim or long term based on your specific needs. Contact our team of experienced cyber experts, political scientists, and data scientists to learn more.
About Oscar
Oscar is a cyber security analyst at Paliscope, mainly focusing on the overlap between threat actors in the digital and physical environment. His primary interest lies in the interconnection between geostrategic trends and the evolving and dynamic threat surface and its implications for organizations in the private and public sectors to promote societal resilience.








